June 21, 2019 Blog Post
Sometimes there is a time that you need to have more control over your outgoing traffic.
I assume that you know what an proxy is and why you need it. I assume you already have it installed and is working.
Most people use the Squid proxy for http/https traffic proxy, but what if you need proxy ssh/sftp connections ?
Why do that ?
Mainly for security reason. Imagine you have a network (subnet) that is not directly connected to the Internet, but you need to allow some outing connection with some hosts on the Internet. A Squid proxy will help you here because you can easily implement a whitelisting or blacklisting.
Implementation
Installing the Squid proxy
If you already have the Squid proxy running, you can ignore this part.
Let's start with the installation of the Squid proxy:
$ sudo yum install -y squid
$ sudo systemctl start squid
This will give us a fully functional Squid service running on the default TCP port 3128.
$ sudo netstat -tlpn|grep 3128
tcp6 0 0 :::3128 :::* LISTEN 11515/(squid-1)
The basic configuration allows you to use it right after starting the service:
$ curl -v -x localhost:3128 http://www.bbc.co.uk -o /dev/null -s
* About to connect() to proxy localhost port 3128 (#0)
* Trying ::1...
* Connected to localhost (::1) port 3128 (#0)
> GET http://www.bbc.co.uk/ HTTP/1.1
> User-Agent: curl/7.29.0
> Host: www.bbc.co.uk
> Accept: */*
> Proxy-Connection: Keep-Alive
>
< HTTP/1.1 301 Moved Permanently
< Server: nginx
< X-BBC-No-Scheme-Rewrite: 1
< X-Cache-Action: HIT
< X-Cache-Hits: 14999
< Vary: X-BBC-Edge-Scheme
< Cache-Control: public, max-age=3600
< X-Cache-Age: 2929
< Content-Type: text/html
< Date: Sun, 23 Jun 2019 08:07:45 GMT
Allowing the Squid to tunnel SSH/SFTP protocol
Squid does not understand the SSH protocol, so it will use CONNECT method to tunnel it.
To allow tunneling of SSH/SFTP connections, open the Squid configuration file (usually /etc/squid/squid.conf) in the editor and add lines in the Accesslist section:
acl SSL_ports port 22
acl Safe_ports port 22 # ssh/sftp
It will look like this:
# Example rule allowing access from your local networks.
# Adapt to list your (internal) IP networks from where browsing
# should be allowed
acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl SSL_ports port 22
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 22 # ssh/sftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
Restart the Squid service and we are ready to test:
$ sudo systemctl restart squidTesting
After adding additional configuration to the Squid configuration file, we are ready to test connectivity.
Linux
$ sftp -oProxyCommand='nc -X connect -x 192.168.56.40:3128 %h %p' 192.168.1.252
test1@192.168.1.252's password:
Connected to 192.168.1.252.
sftp> quit
This same way we use to connect to the sftp server and the ssh console. After confirming that this connection is working, we can add configuration to '~./ssh/config' to enable automatic tunneling:
Host 192.168.1.252
ProxyCommand nc -X connect -x 192.168.56.40:3128 %h %p
ServerAliveInterval 10
Windows
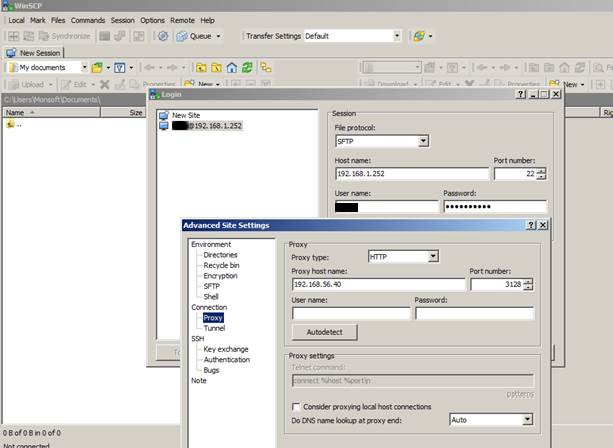
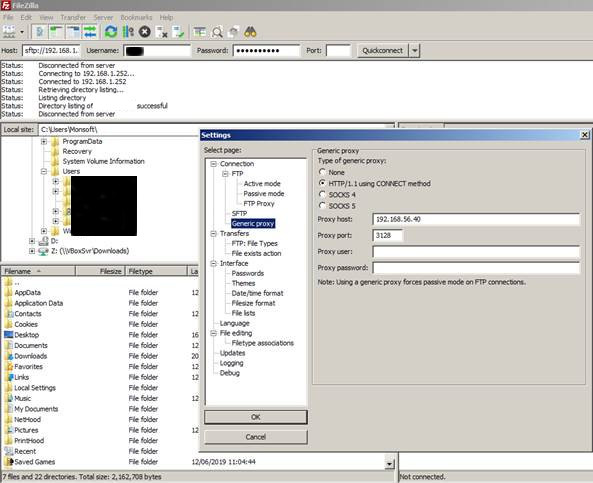
The two most popular SFTP clients on Windows also work with the Squid proxy server.
WinSCP:
FileZilla:
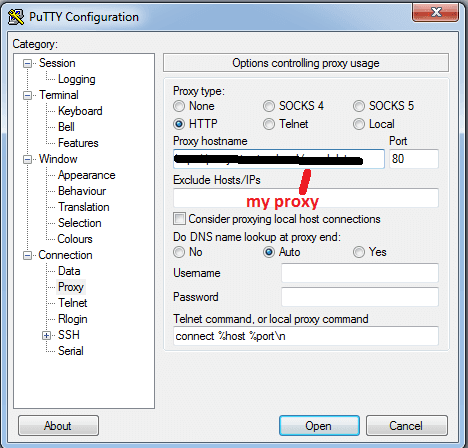
The SSH client Putty also has option of tunnelling the connection via an HTTP proxy: