April 16, 2020 Blog Post
Scammer - a person who commits fraud or participates in a dishonest scheme.
It started with an email I received from my friend who asked me:
I got strange SMS. I don’t know the sender, so can you check if it’s safe ?
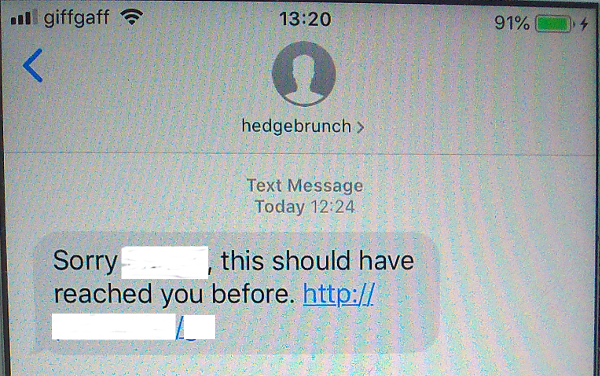
This SMS definitely looks like scam or phishing, so I decided to look closer at its content.
Checking URL
As usual, I started Kali Linux and started testing..
Does the URL still resolving to the IP address ?
root@kali:~/Scripts# host xxxx.com
xxxx.com has address 47.91.xx.xx
Who is the owner of this IP address ?
root@kali:~/Scripts# whois 47.91.xx.xx
# start
NetRange: 47.91.64.0 - 47.91.95.255
CIDR: 47.91.64.0/19
NetName: ALICLOUD-GM
NetHandle: NET-47-91-64-0-1
Parent: AL-3 (NET-47-88-0-0-1)
NetType: Reassigned
OriginAS: AS45102
Customer: ALICLOUD-GM (C06961501)
The IP address belongs to the Alibaba Cloud network.
root@kali:~/Scripts# curl http://xxxxx.com/0
root@kali:~/Scripts#
A simple curl call didn’t bring anything on the screen, but no error occurred, so the URL is still active. Let’s run it in verbose mode:
root@kali:~/Scripts# curl -v http://xxxxx.com/0
> GET /0 HTTP/1.1
> Host: xxxx.com
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Server: nginx/1.16.1
< Date: Thu, 16 Apr 2020 14:08:03 GMT
< Content-Type: text/html; charset=UTF-8
< Transfer-Encoding: chunked
< Connection: keep-alive
< Location: https://wnn.digital/british-government-shaken-by-underground-system?offer_id=16&url_id=82&aff_id=2&source=smse&aff_sub=72572-0415-XXXXXXXXXXXX&aff_unique1=XXXXXXXXXXXXXXXX%40btinternet.com&aff_unique2=44XXXXXXXXXXXX&fname=Last&lname=&email=XXXXXXX%40btinternet.com&phone=44XXXXXXXXXXXX&gi=XXXXXXXXXXXXXXXXXXXXXx&ad_id=46469
< X-Frame-Options: SAMEORIGIN
< X-XSS-Protection: 1; mode=block
< X-Content-Type-Options: nosniff
<
This output shows that the URL used in the SMS is a redirect (HTTP 302) to another page with pre-filled personal data. I ran few more calls and found that when iterating the URL http://xxxxx.com/ZZ where ZZ is from range 0-9, and a-z I can get personal data of different people, so Scammer’s server is leaking victims’ personal data.
Pulling victims' data
The curiosity took place, so I decided to check how many personal records this server was leaking. Sensitive data in this case are within redirection link, so I’m only interested in getting it from every curl call. This was achieved by using curl with -w "%{redirect_url}" option:
root@kali:~/Scripts# curl -w "%{redirect_url}" -o /dev/null -s http://xxxxx.com/0
https://wnn.digital/british-government-shaken-by-underground-system?offer_id=16&url_id=82&aff_id=2&source=smse&aff_sub=72572-0415-XXXXXXXXXXXX&aff_unique1=XXXXXXXXXXXXXXXX%40btinternet.com&aff_unique2=44XXXXXXXXXXXX&fname=Last&lname=&email=XXXXXXX%40btinternet.com&phone=44XXXXXXXXXXXX&gi=XXXXXXXXXXXXXXXXXXXXXx&ad_id=46469
or
root@kali:~/Scripts# curl -w "%{redirect_url}" -o /dev/null -s http://xxxxx.com/00
https://bitcoinrejoin.com/?offer_id=16&url_id=82&aff_id=2&source=smse&aff_sub=72615-0415-XXXXXXXXXXX&aff_unique1=XXXXXXXXXXX%40royalmail.com&aff_unique2=447XXXXX&fname=XXX&lname=XXX&email=XXXXXXXXXXX%40royalmail.com&phone=44XXXXXXXXX&gi=XXXXXXXXXXXXXXXXXXXx&ad_id=61906
It looks much better :)
Now it’s time to do real pull and check how many records I can get from this server. Based on my previous discovery, I created a small script that consist of few loops to iterate over the UR:
#!/bin/bash
for x in {0..9} {a..z};do
curl -w "%{redirect_url}" -o /dev/null -s http://xxxxx.com/$x
echo ""
done
for x in {0..9} {a..z};do
for y in {0..9} {a..z};do
curl -w "%{redirect_url}" -o /dev/null -s http://xxxxx.com/$x$y
echo ""
done
done
A simple script, but it did the “job”.
The script runs for short while and saved all collected data to file. After cleaning the output from empty lines, I received 1008 records with personal data such as first & last name, phone number and email address.
root@kali:~/Scripts# wc -l data.csv
1008 data.csv
Not all records are complete, but this is quite good result …
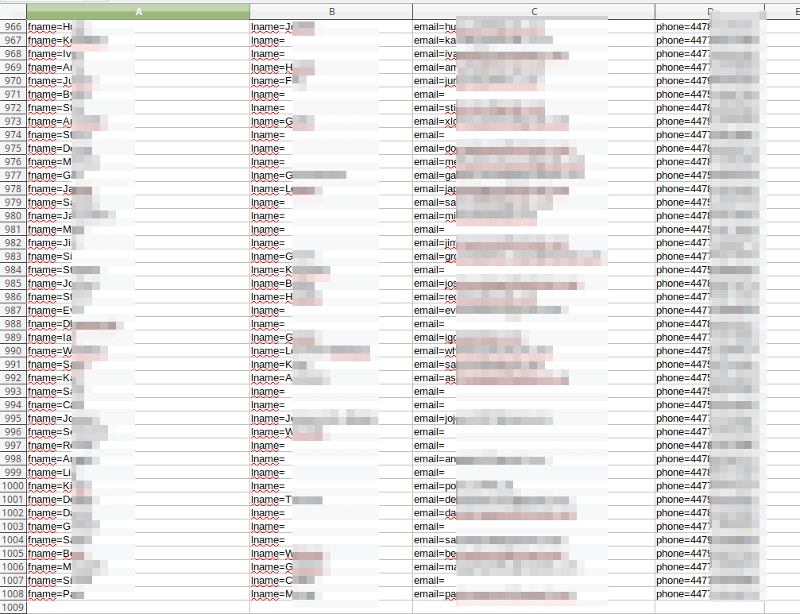
Small data statistic
Based on the collected data, I can see that all phone numbers have the profix +44 (United Kingdom). Most emails are from Gmail and Hotmail:
211 gmail.com
120 hotmail.com
95 hotmail.co.uk
52 yahoo.co.uk
40 yahoo.com
28 icloud.com
24 aol.com
22 btinternet.com
19 outlook.com
11 live.co.uk
8 ymail.com
8 sky.com
6 ntlworld.com
6 msn.com
6 mail.com
5 wp.pl
5 talktalk.net
5 live.com
4 me.com
3 tiscali.co.uk
3 mac.com
2 virginmedia.com
2 tlen.pl
2 o2.pl
2 o2.co.uk
2 gmx.com
1 yandex.ru
1 waitrose.com
1 talk21.com
1 stumpcrosscaverns.co.uk
1 smam.net
1 simmonds1.net
1 royalmail.com
1 rocketmail.com
1 pa-sport.com
1 oxfordhealth.nhs.uk
1 nhs.net
1 meridianglobalservices.com
1 lycos.co.uk
1 linetexinvestments.com
1 leeds.ac.uk
1 interia.pl
1 hotmial.co.uk
1 handbag.com
1 haeck.me.uk
1 gmail.co.uk
1 gmail.con
1 gmai.com
1 globaldatinginsights.com
1 gamil.com
1 fsmail.net
1 falconcouriers.com
1 dunfermline047.wanadoo.co.uk
1 donaldstarkeydesigns.com
1 deepcom.co.uk
1 citi.com
1 btopenworld.com
1 bluerex.co.uk
1 bloxpix.com
1 badmail.biz
1 4gmail.com
Based on this data, I came to the conclusion that they all come from security breaches of UK servers or where purchased from data enrichment companies such as People Data Labs (PDL) and OxyData (OXY). These companies sell your personal data at a low price. Both located in the USA, where General Data Protection Regulation (GDPR) is not followed and no similar law exists.
Reporting security breach
On the same day I found a data leak, I decided to report it to companies involved in hosting/providing any services to Scammer.
The Alibaba Cloud
The server redirecting the host and leaking “Personal Data” is hosted on Alibaba Cloud, so I decided to start with them.
1st, I sent an email to abuse@alibaba-inc.com, which I found on the whois response. No confirmation email, nothing.
2nd, I completed the ‘Alibaba Cloud Abuse Report Form’, providing the same information about data leakage and illegal activity. No confirmation email as well.
The ‘Alibaba Cloud Abuse Claim Form’ is one of the strangest Abuse Form which I have filled out, as it asking you to provide proof of your identification in form of a photo ID. Of course, this is security issue, and I think nobody should do it just to submit an abuse form. I didn’t do it either.
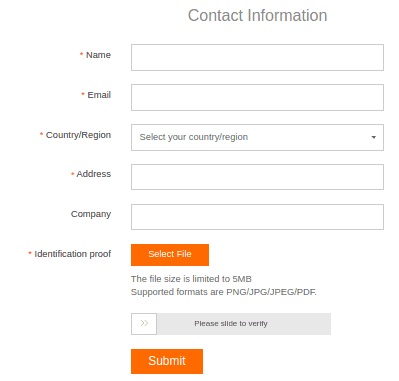
I’m not sure why this practice is allowed, but it clearly makes it difficult to report abuse to this cloud provider and create the perfect place to host servers where illegal content is stored.
The Cloudflare
Both websites https://wnn.digital and https://bitcoinrejoin.com, to which one redirection links were sending visitors, are behind Cloudflare, which “protect them” from “being attacked”. Unfortunately, the real purpose of placing these websites behind Cloudflare was to make them difficult to locate on the Internet, and therefore unable to report to real hosting company. This type of misuse of the Cloudflare service is quite common in spam / phishing campaigns.
https://wnn.digital website looks like proper scam one, becasue nothing really works on it. https://bitcoinrejoin.com looks more “legitimate”. I filled out Cloudflare Abuse Form for them with detailed explanation, but I don’t really expect anything to happen because Cloudflare usually does nothing or does very little (that’s why it is often used in spam / phishing campaigns). Their statement on Abuse From web page explain their actions:
“Because Cloudflare does not have the ability to remove content from a website, it is our practice to forward abuse complaints to entities like the hosting provider and/or website owner to follow up.”
In few words, “we will inform the hosting company about your claim, but we will still provide our service to customer”.
The Police
There is very little what UK Police can do as a server that leaks data is located outside the UK.
Conclusion
I tried to do what I think is right - notify the hosting provider and service providers, but unfortunately until today (3rd day since I filled out all abuse forms) the server that is the source of the data leak is still up and running and there is no response from the Alibaba Cloud team regarding my abuse complain.
Websites reported to Cloudflare are also running.
The lack of response to abuses clearly shows that some service providers do not care about data leakage.
Updates
09.06.2020
I got access to another screenshot of the same type of phishing attack. The same idea, but sent from different phone number and pointing to different redirect website. This time, the URL has more characters as selector (three):
http://xxxxxxx.com/299
To explore this URL, I used slightly different way to generate the dynamic portion of the URL:
#!/bin/bash
TAB=$((echo obase=16; seq 1 $((echo ibase=16; echo FFF) | bc)) | bc|tr [A-Z] [a-z])
for i in $TAB;do
curl -w "%{redirect_url}" -o /dev/null -s http://xxxxxxx.com/$i
echo ""
done
This time the spammer has slightly less personal data records because 767:
# wc -l personal_data_2.csv
767 personal_data_2.csv
All redirects point to https://bitfit.software, which is behind Cloudflare, and the host that hosts the redirect software is located on Alibaba Cloud:
root@kali:~/Scripts# whois 8.209.xx.xx
inetnum: 8.209.64.0 - 8.209.127.255
netname: ALICLOUD-DE
descr: Westendstrabe 28, 60325 Frankfurt am Main
country: DE
I know this may not make sense, but I decided to report this host to Alibaba using different email address anti-spam@list.alibaba-inc.com. No reaction as well. :(